GCP BigQuery
Overview
Google BigQuery, part of Google Cloud Platform, is a data warehousing solution designed for storing, querying, and analyzing large datasets. It offers scalability, SQL-based querying, and integrations with other GCP services and third-party tools.
Below you can find the Aembit configuration required to work with the GCP BigQuery service as a Server Workload using the BigQuery REST API.
Prerequisites
Before proceeding with the configuration, ensure you have the following:
- An active Google Cloud account
- A GCP project with BigQuery enabled
- Data available for querying in BigQuery
Steps to Perform on Google Cloud Console
-
Sign in to the Google Cloud Console and navigate to Service Accounts. Ensure that you are working within a GCP project for which you have authorization.
-
On the Service Accounts dashboard, click Create Service Account located in the top left corner.
- Provide a name for your service account. The ID will be generated based on the account name, but you have the option to edit it. The description field is optional.
- Click the icon next to Email address to copy it and store the address for later.
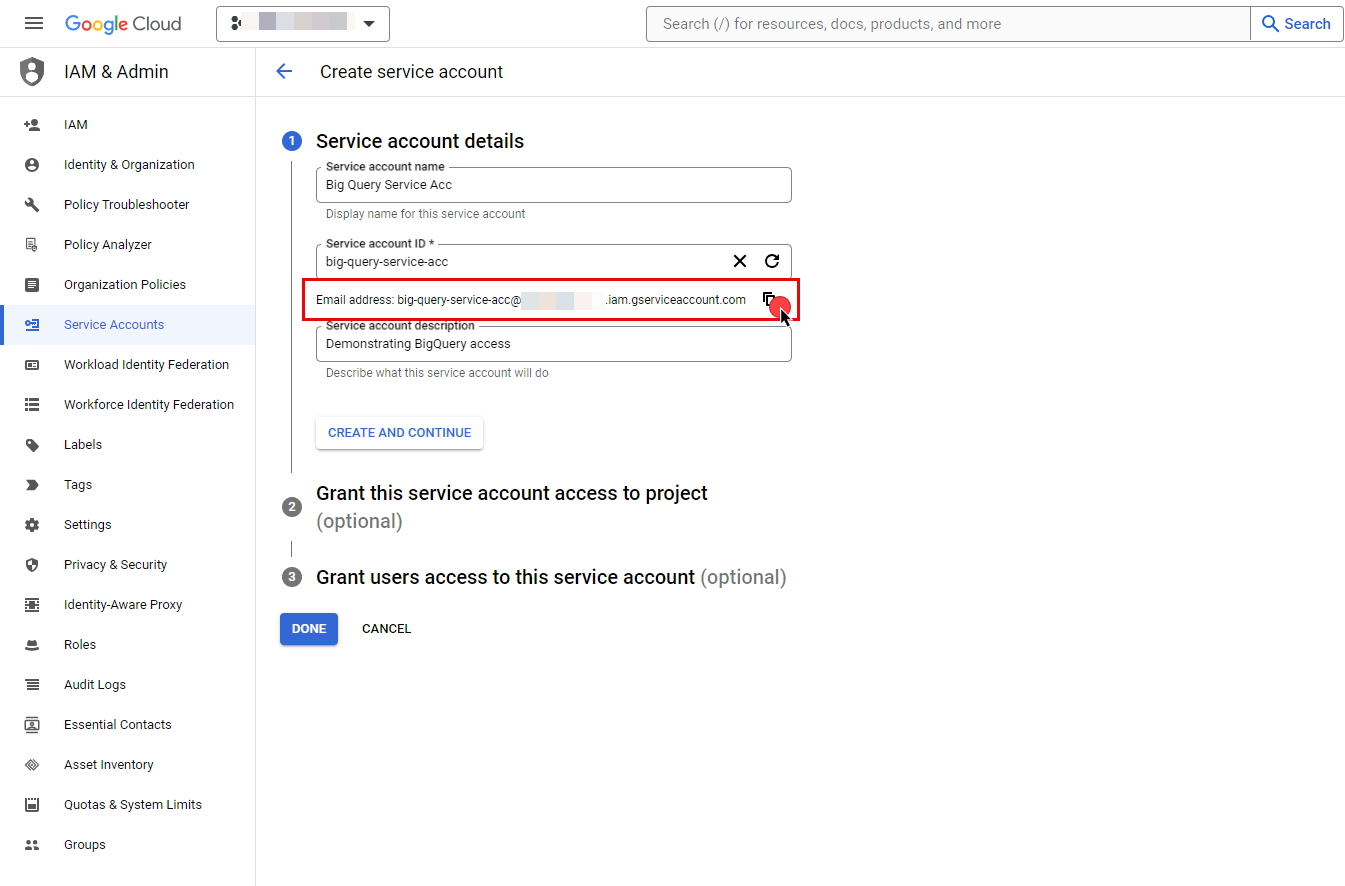
- Click Done.
-
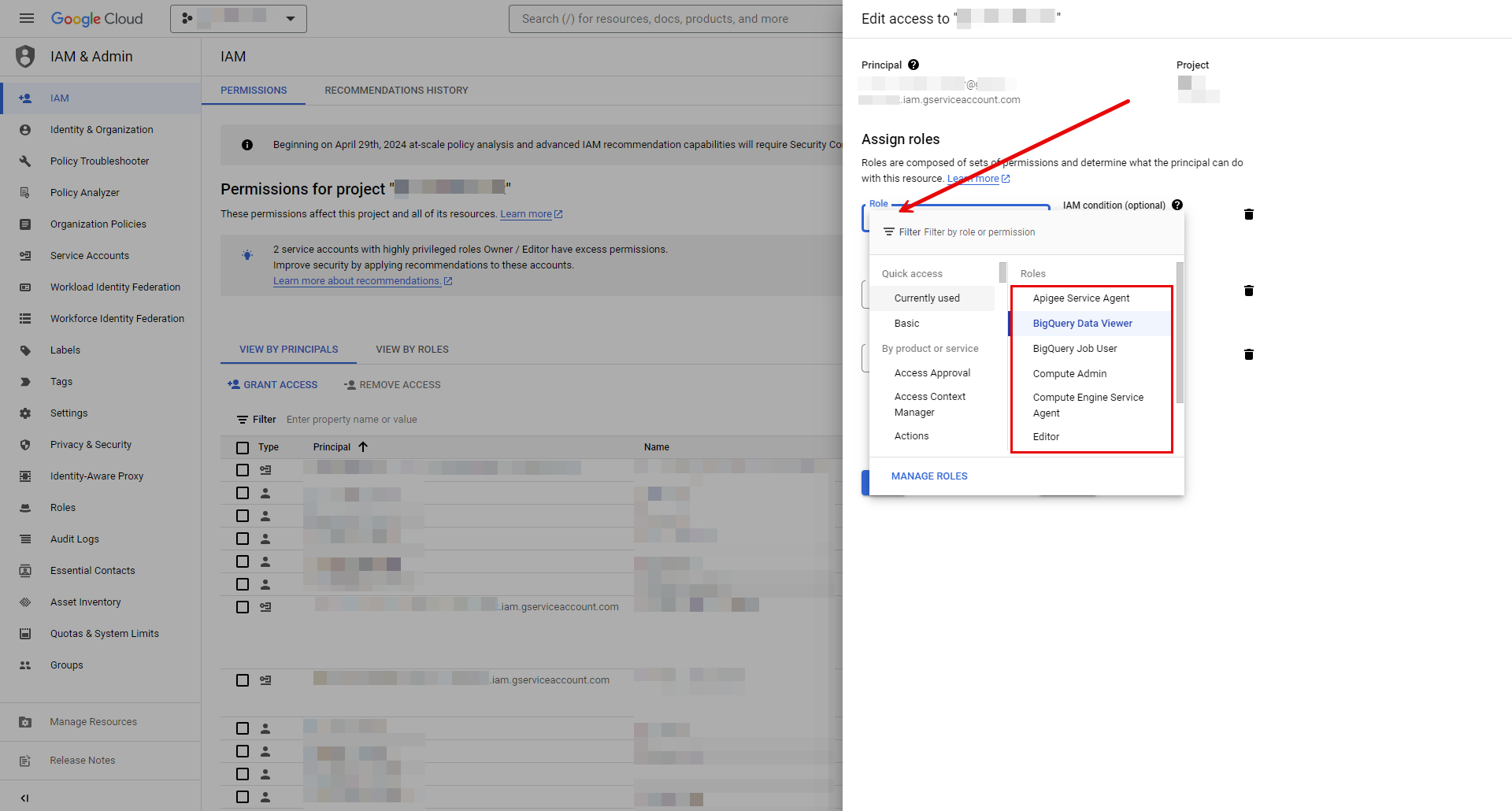
In the left navigation pane, select IAM to access a list of permissions for your project.
-
Find the service account you just created and click the Edit Principal icon(pencil icon).
-
Assign roles to your service account by clicking the drop-down icon and selecting one of the GCP roles that best suits your project needs, then click Save.
-
In the left navigation pane, select Workload Identity Federation, then click the Get Started button.
- Specify a name for your identity pool. The ID will be generated based on the pool name, but you can edit it if needed. The description field is optional; proceed by clicking Continue.
- Next, add a provider to the pool. Select OpenID Connect (OIDC) as the provider option and specify a name for your provider. Again, the ID will be auto-generated, but you can edit it.
- For the Issuer(URL) field, navigate to Aembit UI, create a new Credential Provider, choose Google Workload Identity Federation, and copy the auto-generated Issuer URL, then paste it into the field.
- If you choose to leave the Audiences option set to Default audience, click the Copy to clipboard iconnext to the auto-generated value and store the address for later use in the tenant configuration, then proceed by clicking Continue.
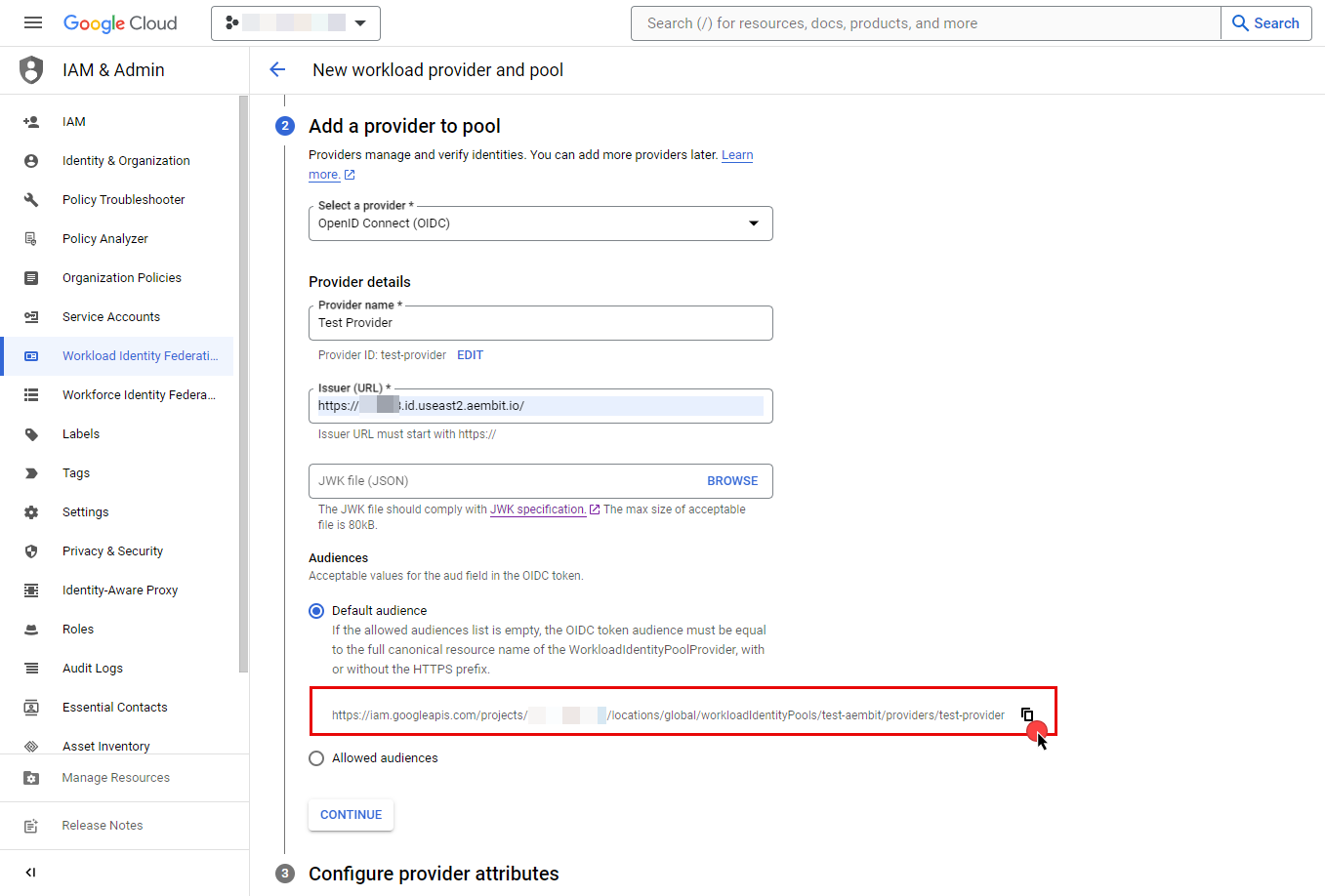
- Specify the provider attribute of assertion.tenant in OIDC 1 and click Save.
-
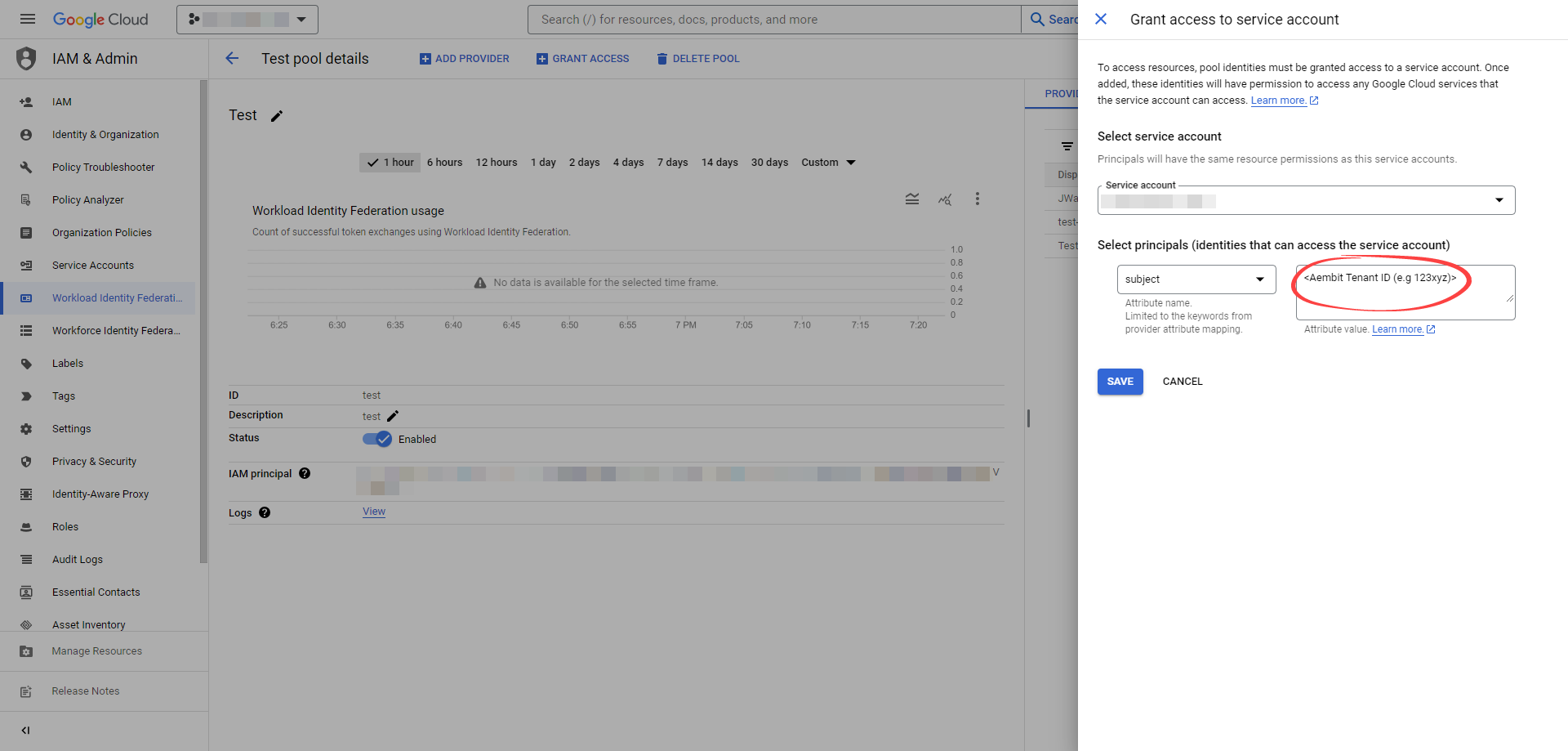
To access resources, pool identities must be granted access to a service account. Within the GCP workload identity pool you just created, click the Grant Access button located in the top ribbon list.
- In the opened dialog, choose the Service Account that you created from the drop-down menu.
- For Attribute name, choose subject from drop-down menu.
- For Attribute value, provide your Aembit Tenant ID. You can find your tenant ID from the URL you use, for example, if the URL is
https://xyz.aembit.io,xyzis your tenant ID. - Proceed with clicking to Continue.
Server Workload Configuration
- Create a new Server Workload.
- Name - Choose a user-friendly name.
- Configure the Service endpoint:
- Host - bigquery.googleapis.com
- Application Protocol - HTTP
- Port - 443 with TLS
- Forward to Port - 443 with TLS
- Authentication method - HTTP Authentication
- Authentication scheme - Bearer
Credential Provider Configuration
- Create a new Credential Provider.
- Name - Choose a user-friendly name.
- Credential Type - Google Workload Identity Federation
- OIDC Issuer URL (Read-Only) - An auto-generated OpenID Connect (OIDC) Issuer URL from Aembit Admin.
- Audience - Provide the audience value for the provider. If the default audience was chosen during provider creation, provide the value previously copied from Google Cloud Console, excluding the http prefix (e.g., //iam.googleapis...).
- Service Account Email - Provide the service account email that was previously copied from Google Cloud Console during service account creation.
- Lifetime - Specify the duration for which the credentials will remain valid.
Client Workload Configuration
Aembit now handles the credentials required to access the Server Workload, eliminating the need for you to manage them directly. You can safely remove any previously used credentials from the Client Workload.
If you access the Server Workload through an SDK or library, it is possible that the SDK/library may still require credentials to be present for initialization purposes. In this scenario, you can provide placeholder credentials. Aembit will overwrite these placeholder credentials with the appropriate ones during the access process.
Access Policy
- Create an Access Policy for a Client Workload to access the GCP BigQuery Server Workload. Assign the newly created Credential Provider to this Access Policy.
Required Features
- You will need to configure the TLS Decrypt feature to work with the GCP BigQuery Server Workload.